Download top and best high-quality free DDOS Protection PNG Transparent Images backgrounds available in various sizes. To view the full PNG size resolution click on any of the below image thumbnail.
License Info: Creative Commons 4.0 BY-NC
A denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator attempts to make a computer or network resource inaccessible to its intended users by interrupting services of a host connected to the Internet for some time or forever. Denial of service is usually done by flooding the targeted computer or resource with unnecessary requests to overwhelm systems and prevent some or all genuine requests from being completed.
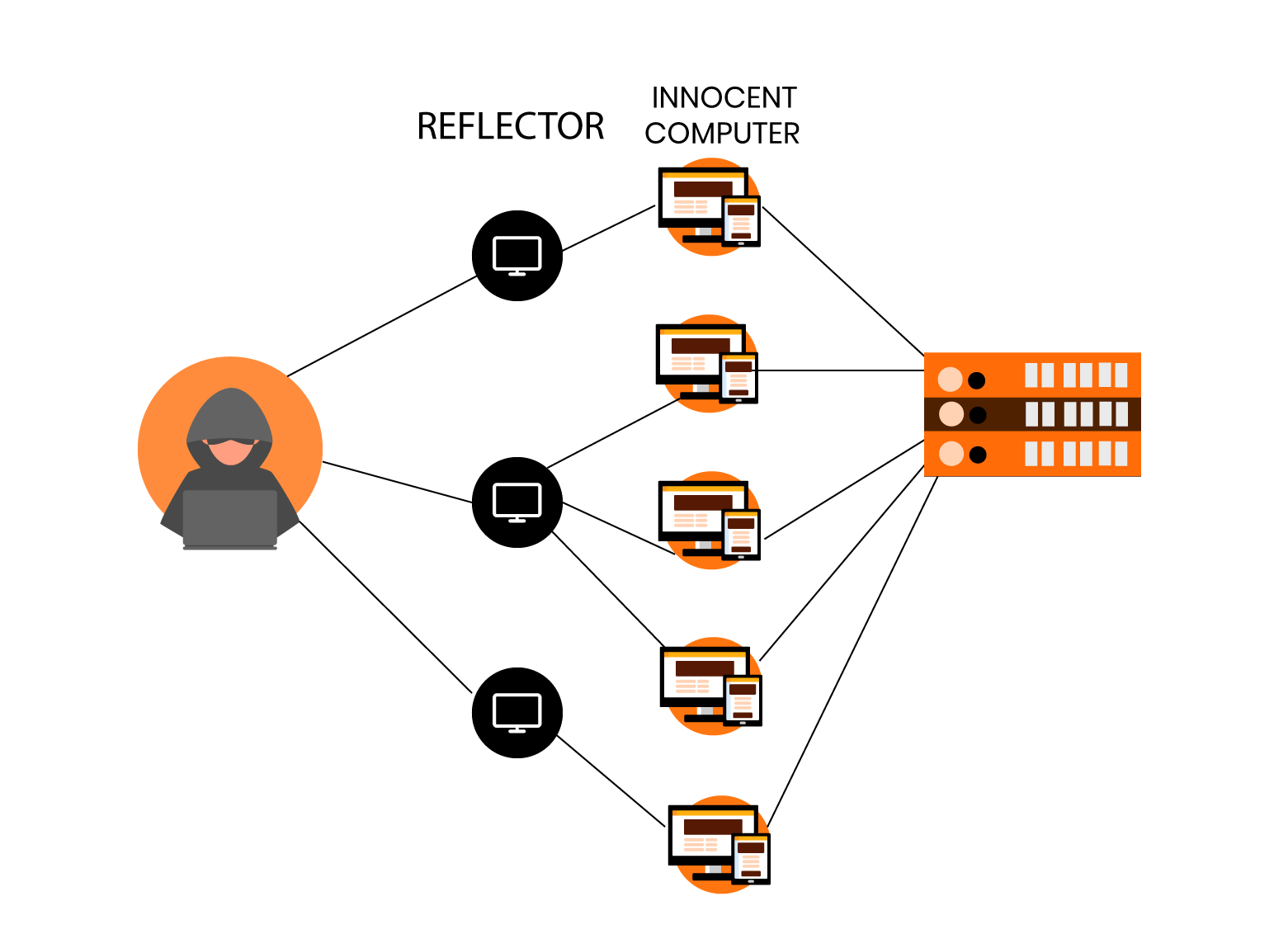
The incoming traffic flooding the target in a distributed denial-of-service attack (DDoS attack) comes from various sources. This makes stopping the attack by blocking a single source difficult.
A DoS or DDoS attack is similar to a crowd of people crowding a shop’s entry door, making it difficult for genuine customers to enter and disrupting business.
To launch their attacks, DoS attackers frequently target high-profile web servers, such as banks or credit card payment gateways. These attacks might be motivated by vengeance, blackmail, or activism.
Denial-of-service attacks are defined as attempts by attackers to prohibit legitimate users from accessing a service. DoS attacks may be divided into two types: those that crash services and those that flood services. The most dangerous attacks are spread out.
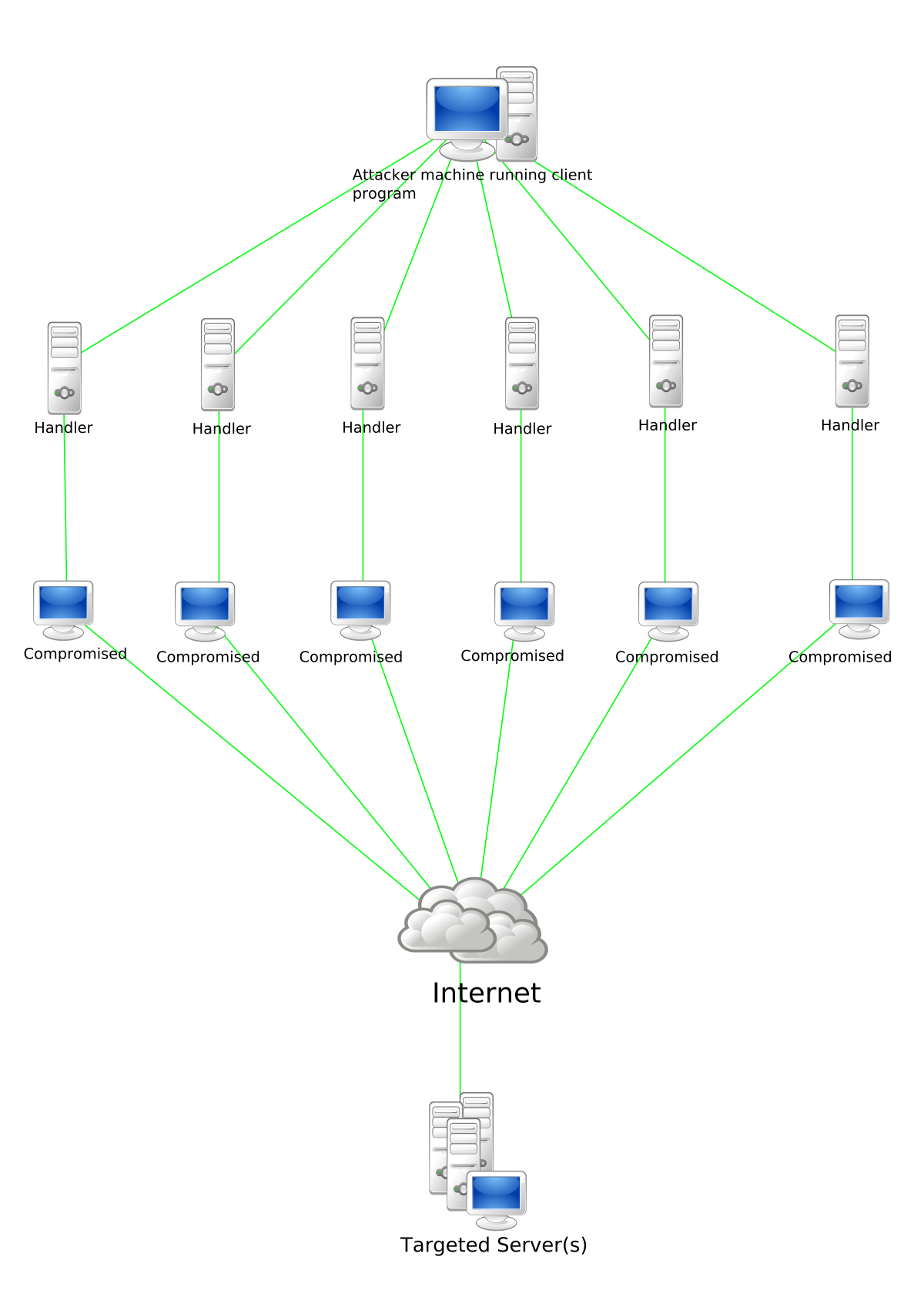
When numerous computers overwhelm the bandwidth or resources of a targeted system, generally one or more web servers, a distributed denial-of-service (DDoS) attack occurs. A DDoS attack employs many distinct IP addresses or computers, sometimes tens of thousands of compromised hosts. A distributed denial of service attack involves more than 3″5 nodes on various networks; a DoS attack with fewer nodes is not a DDoS attack.
Many attack machines can create more attack traffic than a single attack machine. Multiple attack machines are more difficult to switch off than a single attack machine, and each attack machine’s activity can be more stealthy, making it more difficult to monitor and shut down. Because the incoming traffic overwhelming the target comes from various sources, employing ingress filtering alone may not be enough to halt the attack.
It’s also difficult to distinguish between normal user traffic and attack traffic when it’s distributed across numerous origins. Attacks that employ the fabrication of IP sender addresses (IP address spoofing) as an alternative or addition to a DDoS can make detecting and countering the attack even more difficult.
The advantages of the attacker provide a challenge to defense measures. Purchasing more incoming bandwidth than the current volume of the attack, for example, could not be enough because the attacker might just add additional attack machines.
DDoS attacks have grown in size in recent years, reaching a peak of a terabit per second in 2016. UDP flooding, SYN flooding, and DNS amplification are all forms of DDoS attacks.
Download DDOS Protection PNG images transparent gallery.
- DDOS Protection PNG Pic
Resolution: 977 × 230
Size: 46 KB
Image Format: .png
Download
- DDOS Protection PNG Picture
Resolution: 534 × 491
Size: 186 KB
Image Format: .png
Download
- DDOS Protection PNG
Resolution: 512 × 512
Size: 16 KB
Image Format: .png
Download
- DDOS Protection Transparent
Resolution: 512 × 512
Size: 11 KB
Image Format: .png
Download
- DDOS Protection
Resolution: 1200 × 1697
Size: 178 KB
Image Format: .png
Download
- DDOS Protection Background PNG
Resolution: 3538 × 2653
Size: 1369 KB
Image Format: .png
Download
- DDOS Protection No Background
Resolution: 461 × 242
Size: 99 KB
Image Format: .png
Download
- DDOS Protection PNG Clipart
Resolution: 512 × 512
Size: 35 KB
Image Format: .png
Download
- DDOS Protection PNG Cutout
Resolution: 1200 × 1400
Size: 51 KB
Image Format: .png
Download
- DDOS Protection PNG File
Resolution: 512 × 512
Size: 50 KB
Image Format: .png
Download
- DDOS Protection PNG Free Image
Resolution: 1005 × 693
Size: 122 KB
Image Format: .png
Download
- DDOS Protection PNG HD Image
Resolution: 565 × 565
Size: 14 KB
Image Format: .png
Download
- DDOS Protection PNG Image File
Resolution: 797 × 401
Size: 40 KB
Image Format: .png
Download
- DDOS Protection PNG Image HD
Resolution: 813 × 741
Size: 193 KB
Image Format: .png
Download
- DDOS Protection PNG Image
Resolution: 512 × 512
Size: 47 KB
Image Format: .png
Download
- DDOS Protection PNG Images HD
Resolution: 673 × 490
Size: 38 KB
Image Format: .png
Download
- DDOS Protection PNG Images
Resolution: 500 × 300
Size: 16 KB
Image Format: .png
Download
- DDOS Protection PNG Photo
Resolution: 1561 × 1132
Size: 56 KB
Image Format: .png
Download
- DDOS Protection PNG Photos
Resolution: 645 × 389
Size: 6 KB
Image Format: .png
Download