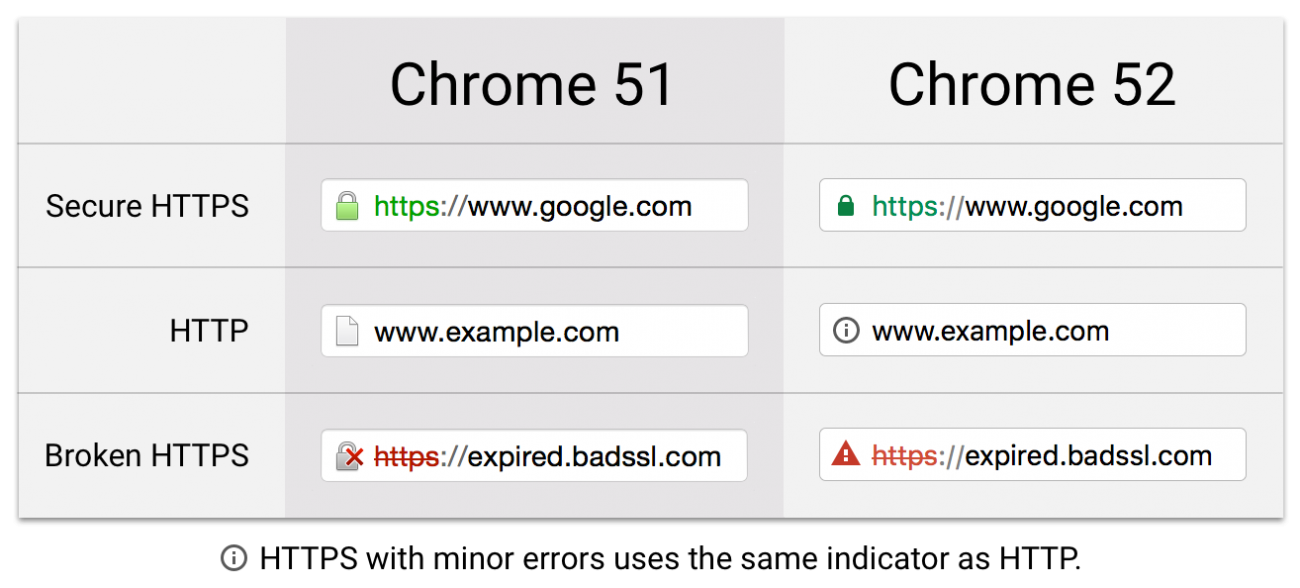
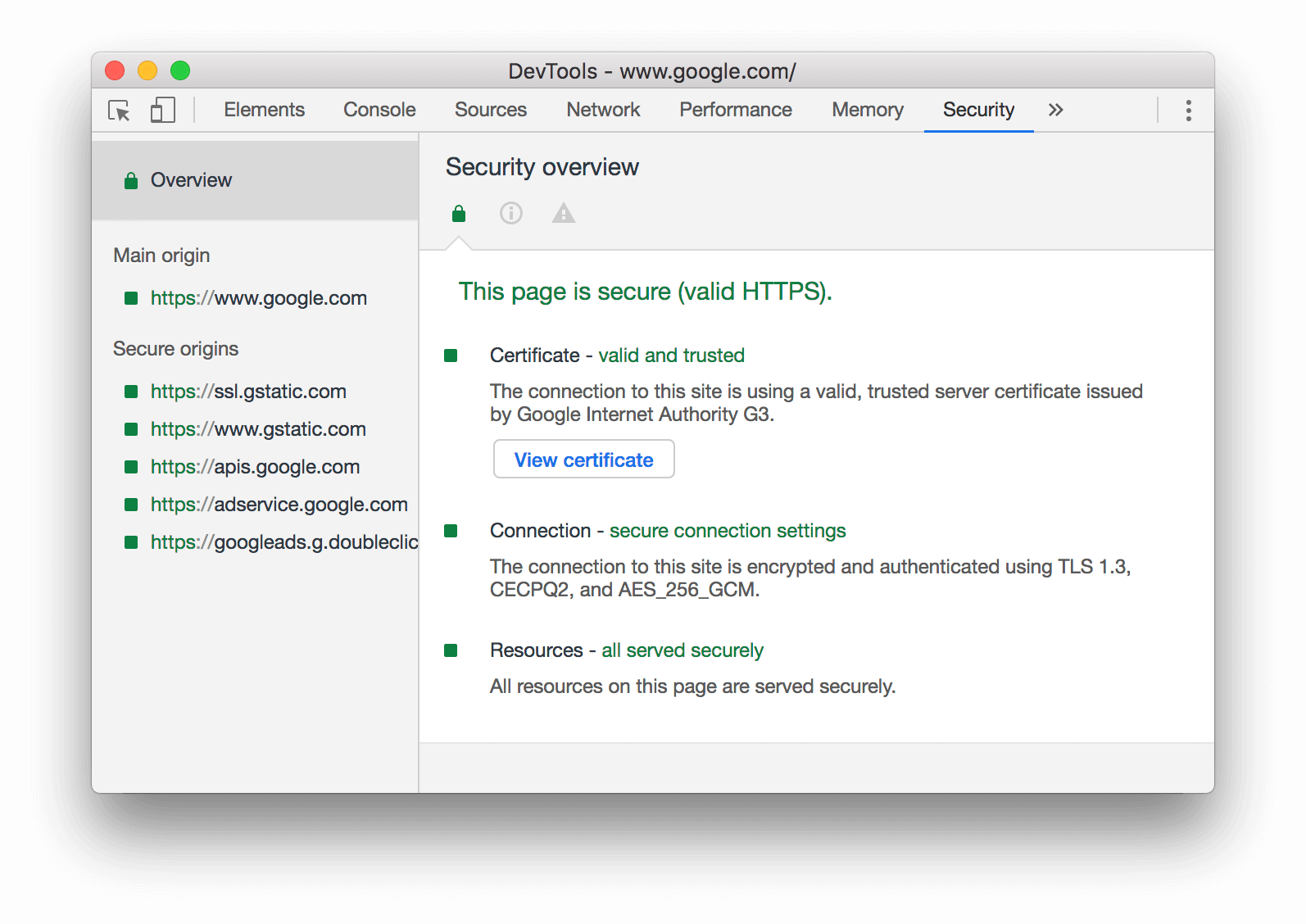
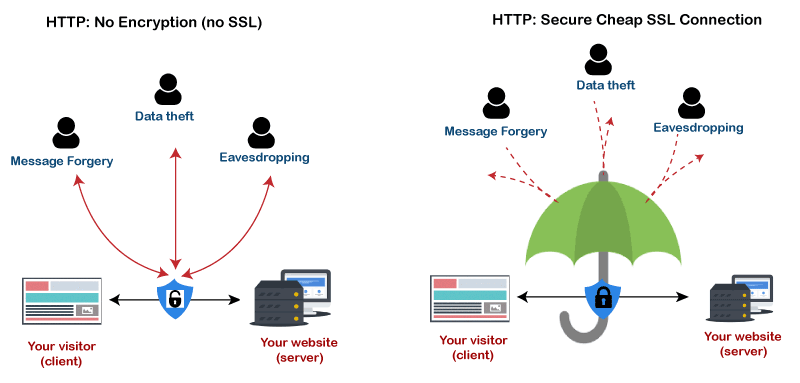
Download top and best high-quality free Secure HTTPS PNG Transparent Images backgrounds available in various sizes. To view the full PNG size resolution click on any of the below image thumbnail.
License Info: Creative Commons 4.0 BY-NC
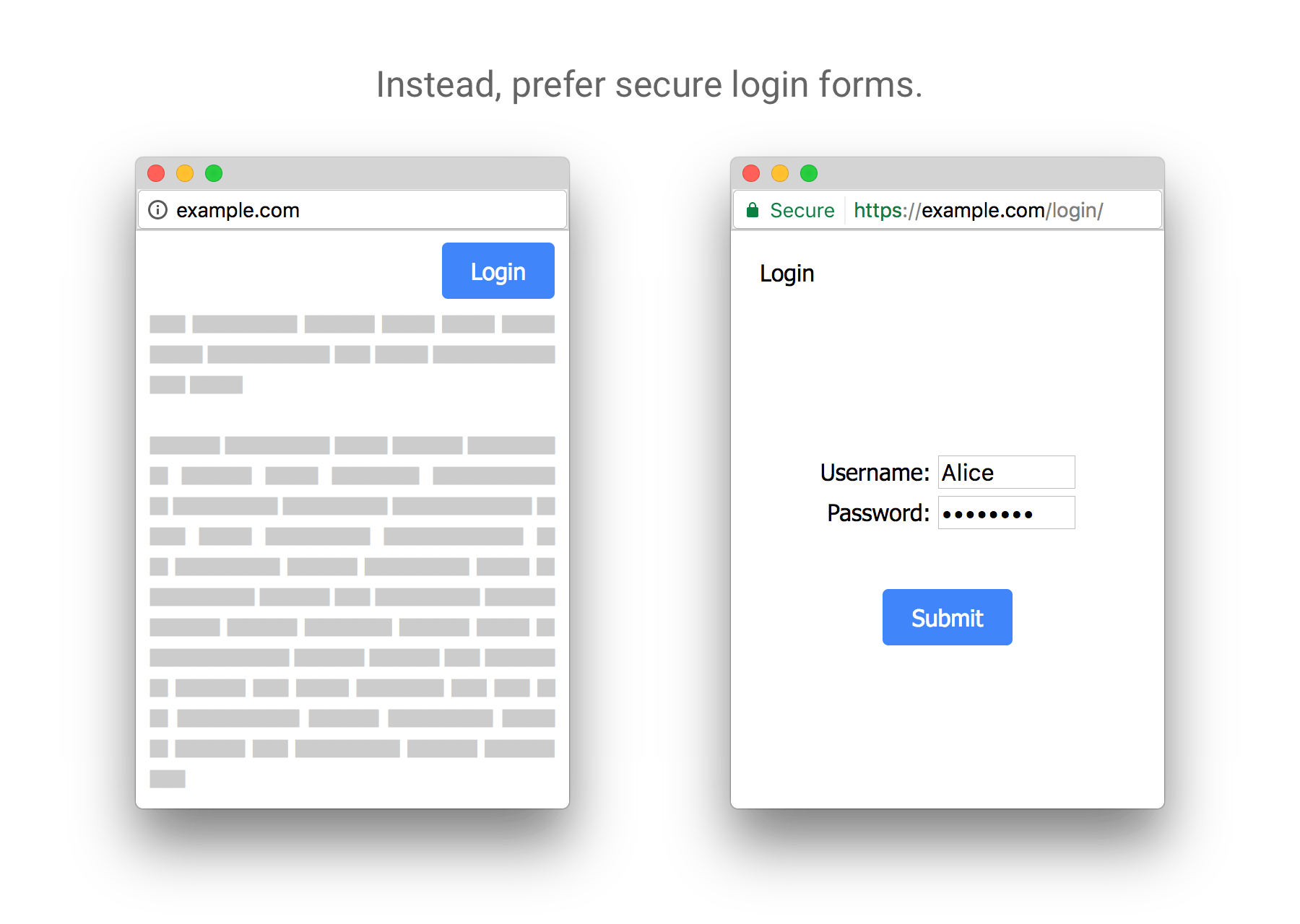
HTTPS (Hypertext Transfer Protocol Secure) is a Hypertext Transfer Protocol (HTTP) enhancement (HTTP). It is extensively used on the Internet and is utilized for secure communication over a computer network. TLS (Transport Layer Security) or Secure Sockets Layer (previously Secure Sockets Layer) encrypts the communication protocol in HTTPS (SSL). As a result, the protocol is sometimes known as HTTP over TLS or HTTP over SSL.
The authentication of the accessible website, as well as the privacy and integrity of the exchanged data while in transit, are the primary objectives for HTTPS. It defends against man-in-the-middle attacks, and bidirectional encryption protects communications between a client and a server from eavesdropping and alteration. HTTPS authentication necessitates the signing of server-side digital certificates by a trustworthy third party.
Due to the high cost of this procedure, properly authenticated HTTPS connections were previously exclusively found on secure financial transaction services and other secure corporate information systems on the Internet. The protocol gained traction in 2016 because to a campaign coordinated by the Electronic Frontier Foundation and supported by web browser makers.
The protocol gained traction in 2016 because to a campaign coordinated by the Electronic Frontier Foundation and supported by web browser makers. HTTPS is increasingly more often used by online users than HTTP, principally to ensure page authenticity on all sorts of websites, secure accounts, and keep user communications, identity, and web browsing secret.
The HTTPS system uses the same Uniform Resource Identifier (URI) scheme as the HTTP scheme. HTTPS, on the other hand, instructs the browser to encrypt the traffic with an additional SSL/TLS layer. SSL/TLS is particularly well suited to HTTP since it can provide some security even if only one side of the conversation is authorized.
This is the situation with HTTP transactions over the Internet, where the client normally just authenticates the server (by inspecting the server’s certificate).
Over an unsecured network, HTTPS establishes a secure channel. If appropriate encryption suites are used and the server certificate is validated and trusted, this provides decent security against eavesdroppers and man-in-the-middle attacks.
Because HTTPS encrypts the entire HTTP protocol by piggybacking it on top of TLS, the entire HTTP protocol may be encrypted. The request URL (which web page was requested), query parameters, headers, and cookies are all part of this (which often contain identifying information about the user).
HTTPS, on the other hand, cannot safeguard the publication of website addresses and port numbers since they are required to be part of the underlying TCP/IP protocols.
In reality, this implies that eavesdroppers may infer a user’s IP address and port number, as well as the quantity of data sent and the length of the conversation, even from a well configured web server.
Based on certificate authorities that come pre-installed in their software, web browsers know how to trust HTTPS websites. Web browser designers trust certificate authority to offer genuine certificates in this way. As a result, a user should only trust an HTTPS connection to a website if all of the following conditions are met:
The user believes that the browser software is successfully implementing HTTPS and that the certificate authorities are pre-installed.
The certificate authority is trusted by the user to vouch for only authentic websites.
The website displays a legitimate certificate, indicating that it was signed by a reputable organization.
The certificate correctly identifies the website (for example, when the browser accesses “https://example.com,” the certificate obtained is for “example.com” and not for any other organization).
The user believes that the protocol’s encryption layer (SSL/TLS) provides enough protection against eavesdroppers.
HTTPS is extremely critical when using unsecured networks or networks that might be tampered with. Insecure networks, such as public Wi-Fi access points, enable anybody on the same local network to sniff packets and uncover sensitive data that isn’t secured by HTTPS.
Furthermore, some free and paid WLAN networks have been spotted meddling with webpages by using packet injection to broadcast their own advertisements on other websites. This approach may be used maliciously in a variety of ways, including putting malware onto websites and stealing users’ personal data.
Malicious Tor nodes might otherwise destroy or change the information travelling through them in an unsecured manner, and introduce malware into the connection, hence HTTPS is also required for communications across the Tor network. One of the reasons why the Electronic Frontier Foundation and the Tor Project developed HTTPS Everywhere, which is incorporated in Tor Browser, is to address this issue.
Download Secure HTTPS PNG images transparent gallery.
- Secure HTTPS Green Symbol
Resolution: 512 × 512
Size: 16 KB
Image Format: .png
Download
- Secure HTTPS Connection
Resolution: 512 × 512
Size: 23 KB
Image Format: .png
Download
- Secure HTTPS Transparent
Resolution: 519 × 231
Size: 63 KB
Image Format: .png
Download
- Secure HTTPS PNG Picture
Resolution: 760 × 400
Size: 10 KB
Image Format: .png
Download
- Secure HTTPS PNG HD Image
Resolution: 1980 × 1420
Size: 243 KB
Image Format: .png
Download
- Secure HTTPS PNG
Resolution: 1600 × 955
Size: 249 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG File
Resolution: 800 × 400
Size: 66 KB
Image Format: .png
Download
- Secure HTTPS PNG Cutout
Resolution: 511 × 496
Size: 9 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG Photo
Resolution: 600 × 420
Size: 69 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG Image
Resolution: 512 × 512
Size: 35 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG Images
Resolution: 1000 × 345
Size: 232 KB
Image Format: .png
Download
- Secure HTTPS PNG Photos
Resolution: 3104 × 1008
Size: 202 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG Photo
Resolution: 1300 × 588
Size: 371 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG Photos
Resolution: 1030 × 903
Size: 428 KB
Image Format: .png
Download
- Secure HTTPS PNG Image HD
Resolution: 1594 × 1128
Size: 76 KB
Image Format: .png
Download
- Secure HTTPS PNG Image
Resolution: 626 × 366
Size: 89 KB
Image Format: .png
Download
- Secure HTTPS PNG Clipart
Resolution: 800 × 383
Size: 16 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG Cutout
Resolution: 1200 × 630
Size: 20 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG Cutout
Resolution: 670 × 240
Size: 13 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG Image
Resolution: 600 × 299
Size: 4 KB
Image Format: .png
Download
- Secure HTTPS PNG Photo
Resolution: 700 × 517
Size: 99 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG File
Resolution: 512 × 512
Size: 5 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG Pic
Resolution: 512 × 512
Size: 25 KB
Image Format: .png
Download
- Secure HTTPS
Resolution: 735 × 491
Size: 68 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG
Resolution: 512 × 512
Size: 20 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG Images
Resolution: 525 × 342
Size: 94 KB
Image Format: .png
Download
- Secure HTTPS PNG Pic
Resolution: 1024 × 497
Size: 17 KB
Image Format: .png
Download
- Secure HTTPS PNG File
Resolution: 1800 × 1280
Size: 39 KB
Image Format: .png
Download
- Secure HTTPS PNG Images
Resolution: 1800 × 1280
Size: 33 KB
Image Format: .png
Download
- Secure HTTPS Green Symbol PNG Pic
Resolution: 1906 × 2006
Size: 39 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG
Resolution: 512 × 512
Size: 14 KB
Image Format: .png
Download
- Secure HTTPS Connection PNG Photos
Resolution: 652 × 300
Size: 64 KB
Image Format: .png
Download